Note: All Treasury Software security is applied on an account by account basis.
There are two components to Treasury Software security:
--client-based
--server-based
Server based security - 'Gold Standard'
Server-based security is Microsoft SQL Server based and is first addressed during account creation and setup. It centers around the user's Windows or SQL Server login ID and the membership of the groups/roles that the individual belongs to.
Based on the membership, the user will have access to or be denied to the various SQL Server databases. There is a one to one relationship between databases and accounts.
SQL Server is maintained according to your corporate security policies outside of Treasury Software by your database administrator (DBA) with Microsoft's SQL Server Management Studio.
Treasury Software products on SQL Server, with SQL Server security maintained - is the strongest form of security we can deliver. SQL Server is required by many Government agencies and according to corporate bank policy. SQL Server security is often viewed as the 'Gold Standard' of security.
Client-based security
The following articles cover client-based security.
Treasury Software also provides two levels of client based security:
--user authentication - simple access to software
--feature-level access - segregation of duties - requires SQL Server with and Treasury Software Enterprise license
Holistic Approach
While we are proud of our client-based security features - if only client-based security is implemented - it will merely be an inconvenience to those seeking to commit fraud.
Security is only as effective as the weakest link in the chain.
Locking down the 'front door' (client), only to leave the 'back door' (server-data) open is not an ideal security model.
Adding to security concerns - The input to Treasury Software is an unprotected file - typically a spreadsheet, and the output for ACH Universal and Positive Pay is an ASCII file.
Client workstation access control
For those environments requiring high security, we highly recommend the use of Windows Operating System and Network Operating System based features, to limit physical and remote access to the Treasury Software client.
Setup
Login - setup
To access the login screen, from the main menu select Settings->Access Control.
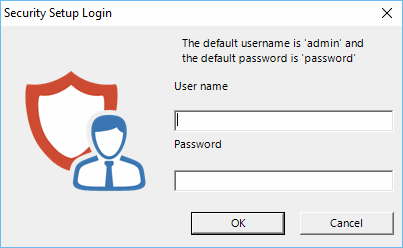
Default User name admin
Default Password password
Once logged in (only an admin can pass through setup security), you will be at the security main page.
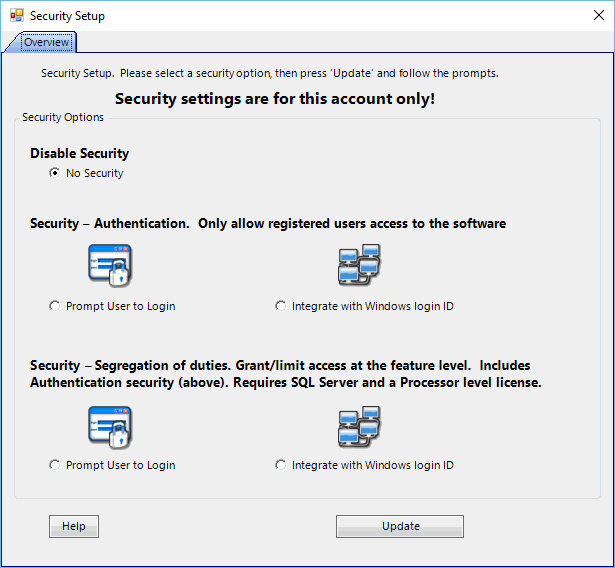
|
Prompt User |
Integrate with Windows |
|
|
Authentication |
Challenge screen prompting the user to login each time the user starts the software and then determines whether access should be granted. |
Uses the Windows Login ID to authenticate and then determines whether access should be granted. |
|
|
|
|
Multiple Accounts - Security is applied on an account by account basis
If you have more than one account, you will need to enter into each account you want to protect and make your security selection.
Tips:
--Do not put security on the Sample account (do not place 'real' account numbers, etc.. in the sample setup)
--Change the default admin password
--Use a Windows Operating Screen screen saver with password protection






